@
@branzu_84 Thanks for the reply! I do know that iMessage in general was enabled. I am trying to find out if this setting was enabled
https://support.apple.com/en-us/HT208532. I also took a checkm8 extraction from an iOS 13 device and analyzed the CloudConfigurationDetails.plist, com.apple.assistant.backedup.plist, and om.apple.CoreDuet.plist but none specfically list iMessage for iCloud or reference it. The most promising artifact so far appears to be com.apple.madrid.plist, with it's
CloudKitSyncingEnabled = :true/false; key and value but I have not yet got an extraction with iMessage for iCloud enabled to compare to (iOS 13 extractions with iMessage for iCloud disabled displayed false as the value, but i have not yet been able to compare a com.apple.madrid.plist from an iOS 13 extraction that has it enabled)




 Waiting until new updates are validated before you are able to use them
Waiting until new updates are validated before you are able to use them

 This is a bit like all those conversations at the bar at conferences !
This is a bit like all those conversations at the bar at conferences !
 )
)



 Paging
Paging 




















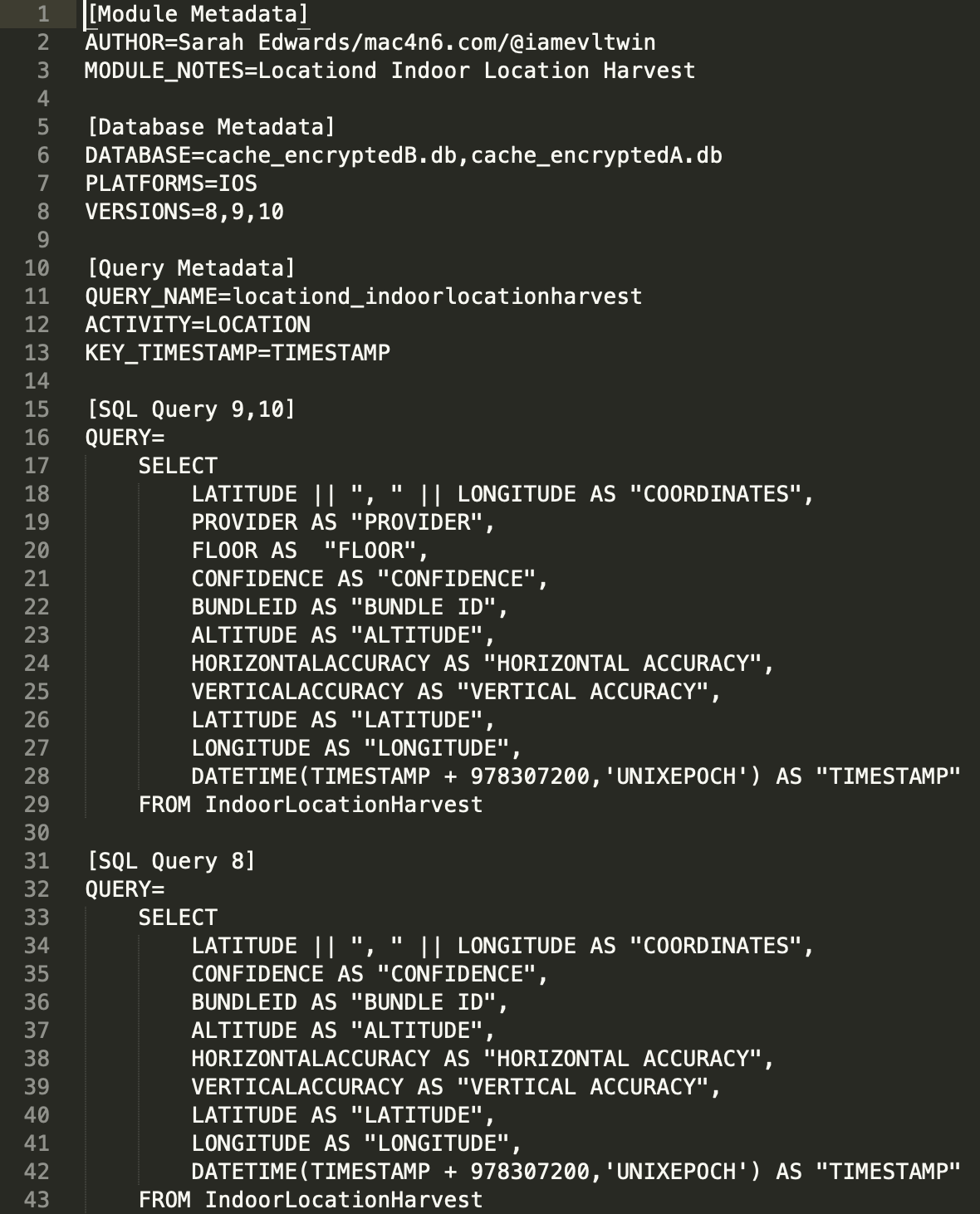


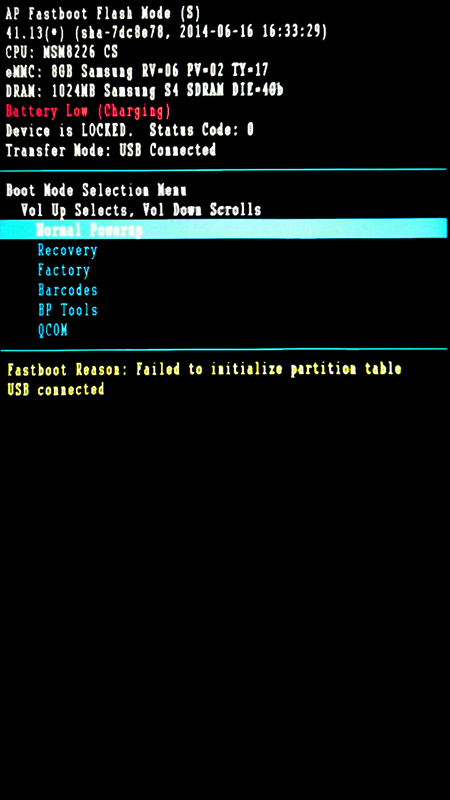
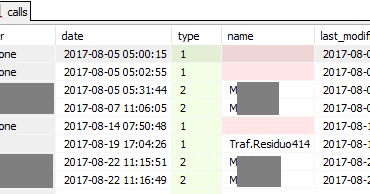
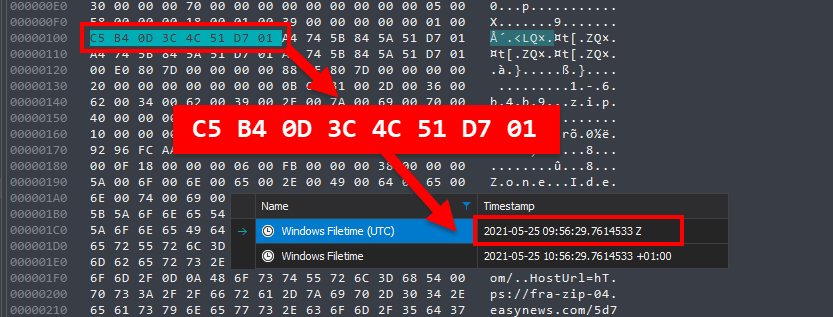
 ! Execpt for the gmt+2... Dates in this results inclue or not this 2hours ?
! Execpt for the gmt+2... Dates in this results inclue or not this 2hours ?








 but this db no longer exists
but this db no longer exists 










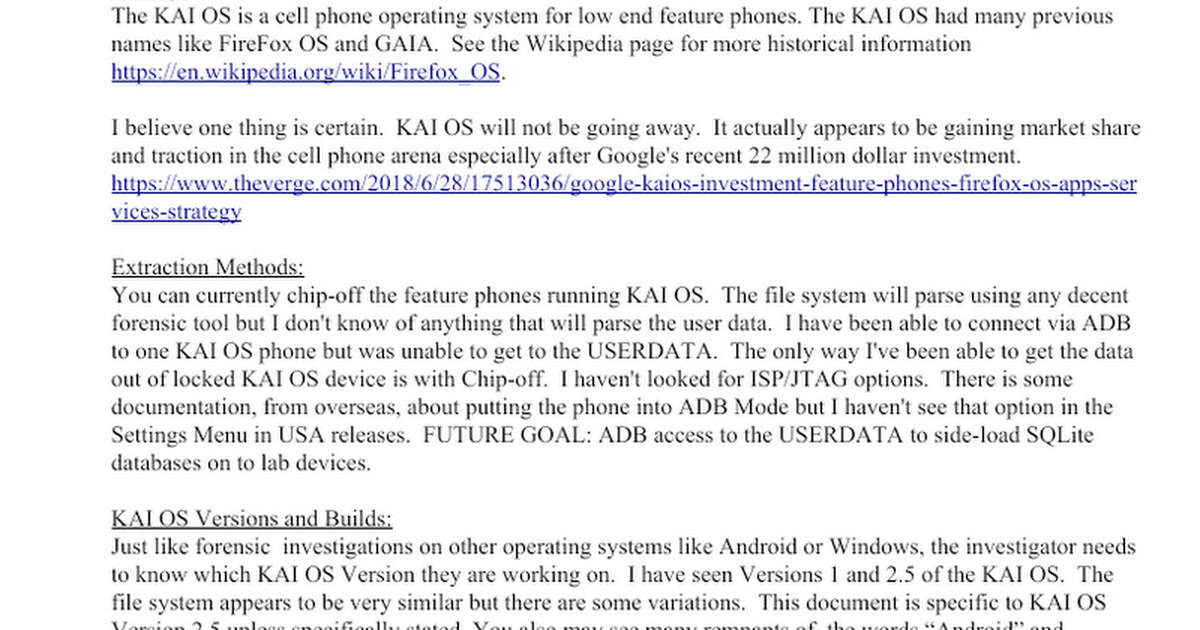




























 ️
️


















 modeltype as i posted above.... shame on you
modeltype as i posted above.... shame on you







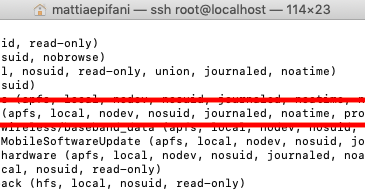
 Since this is ios 12 2 no jb so no possibility to have more information
Since this is ios 12 2 no jb so no possibility to have more information even the filestructure is build as on the device.
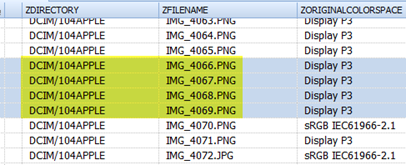
.. and the namens of the attachments are not in Original State i think...
even the filestructure is build as on the device.
.. and the namens of the attachments are not in Original State i think...














 Nokia LUMIA 650 with windows 10
Nokia LUMIA 650 with windows 10 



























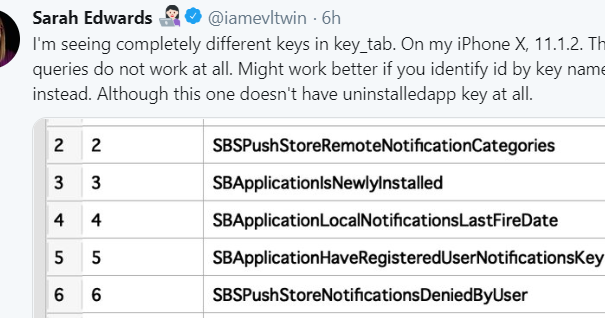


















































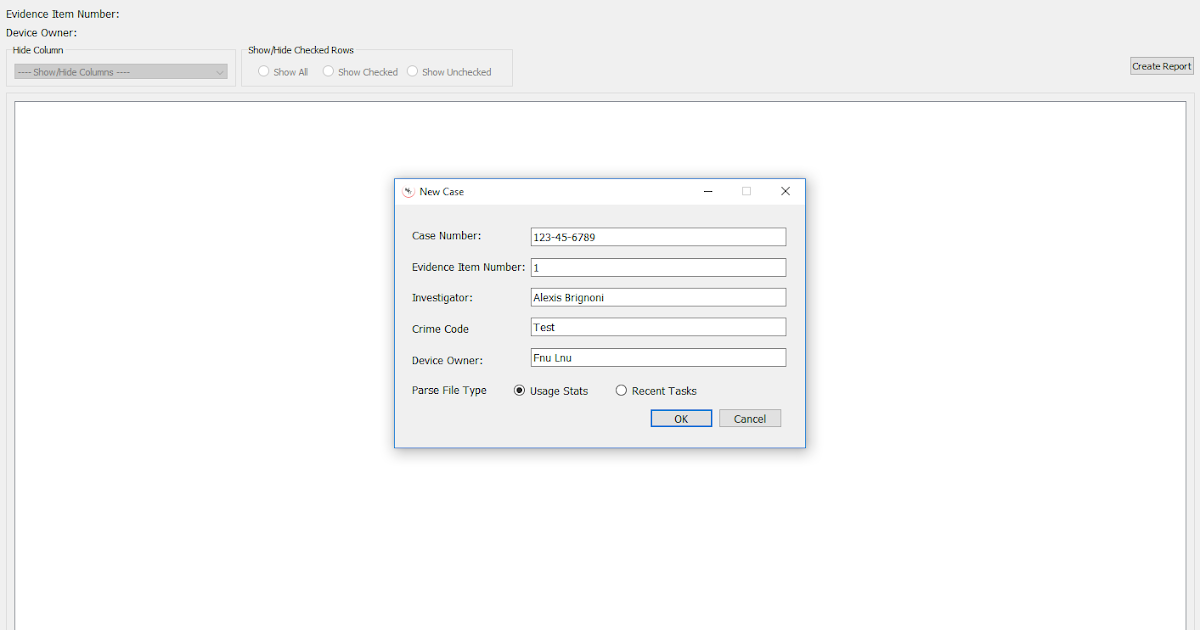




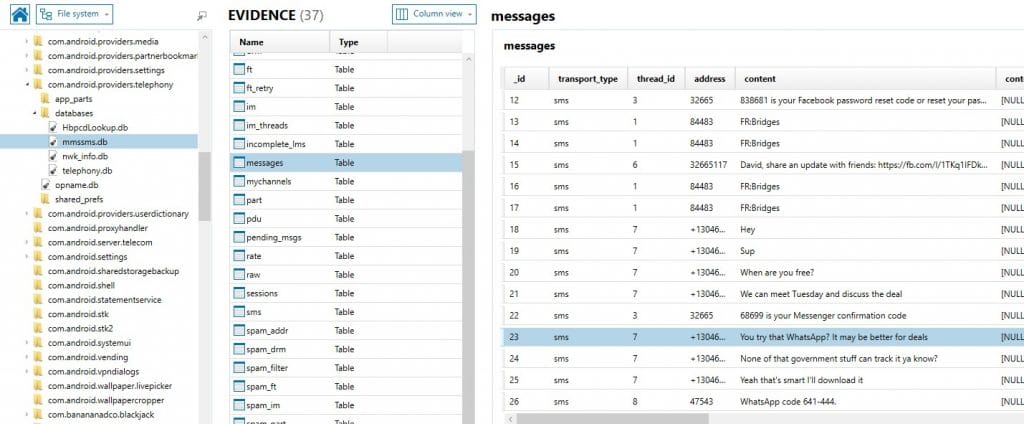


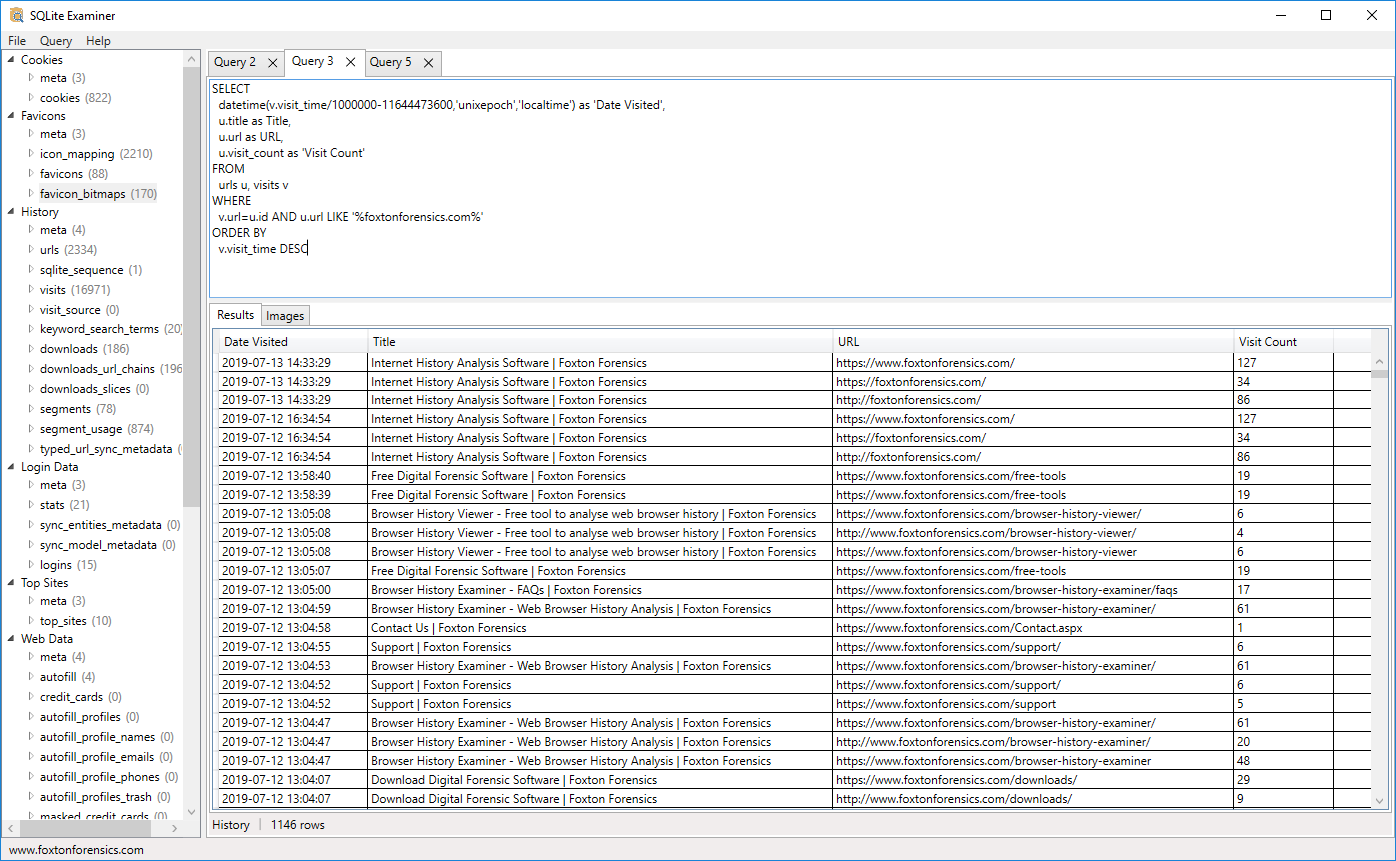


 I, unfortunately, am not...yet...
I, unfortunately, am not...yet...


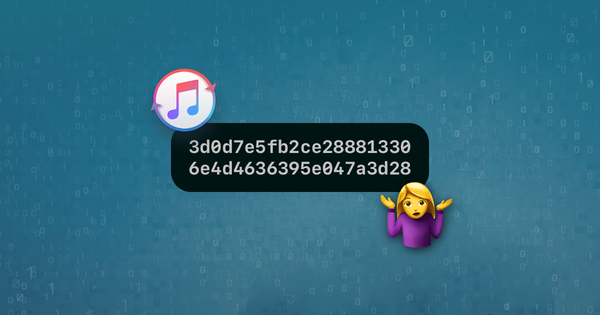
 tested, imported old .bin (made with infinity-dongle) with profile "spreadtrum 6531 generic"... successssssss
tested, imported old .bin (made with infinity-dongle) with profile "spreadtrum 6531 generic"... successssssss

















 ✌
✌


















































































































 and then on to a BAR
and then on to a BAR  and at the end of the night into a TAR (Taxi ARchive)
and at the end of the night into a TAR (Taxi ARchive)  or maybe a ZIPpy coat and scarf
or maybe a ZIPpy coat and scarf  if it's chilly for a walk home... Happy Friday everyone from all of us
if it's chilly for a walk home... Happy Friday everyone from all of us 
















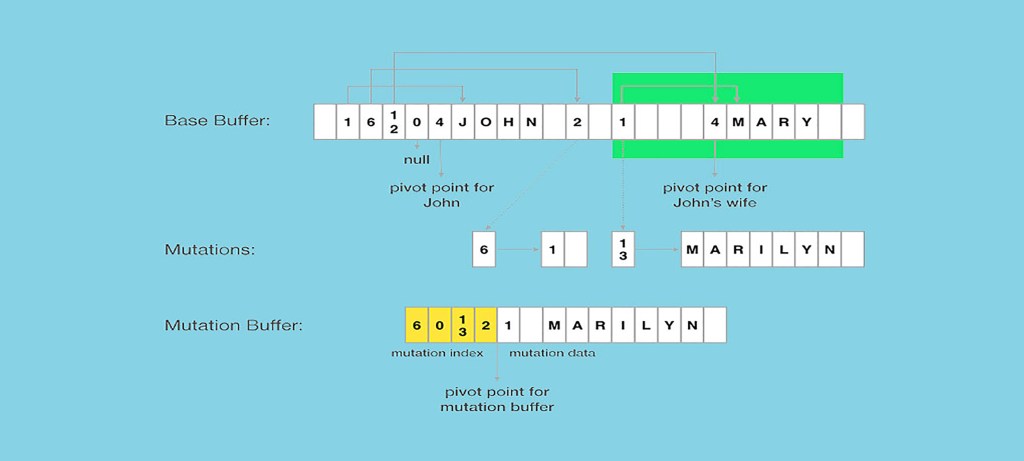
 ♂️
♂️




























 New xLEAPP usability updates!!!
New xLEAPP usability updates!!!
 No need to select extraction type
No need to select extraction type
 Select only the artifacts you want
Select only the artifacts you want
 More concise GUI
Thanks to oleag4n6 (
More concise GUI
Thanks to oleag4n6 (


































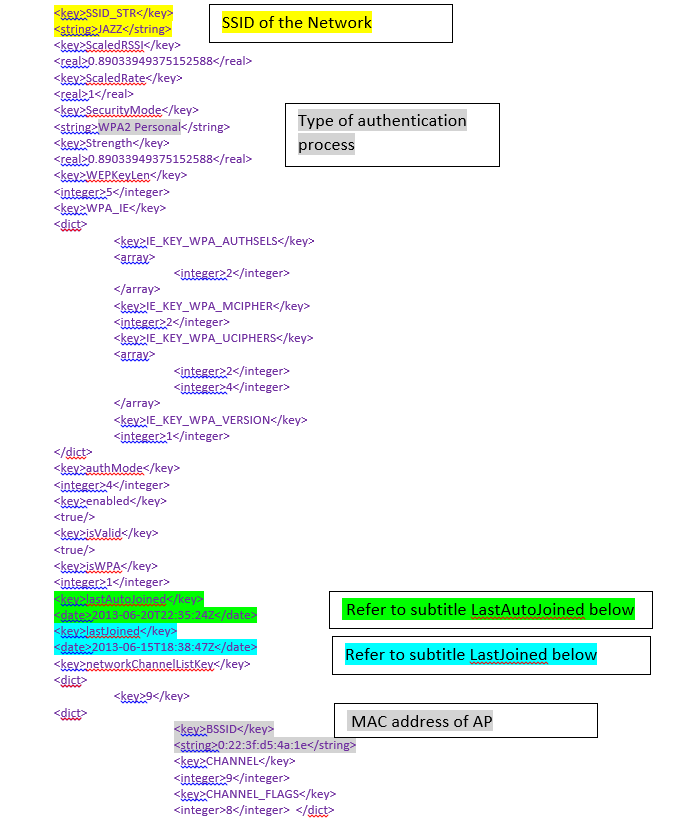






































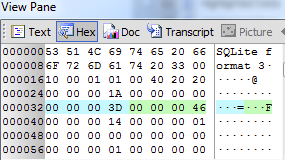






















 and if you want a quick way of decrypting the files it works with online tools like the one found on
and if you want a quick way of decrypting the files it works with online tools like the one found on 












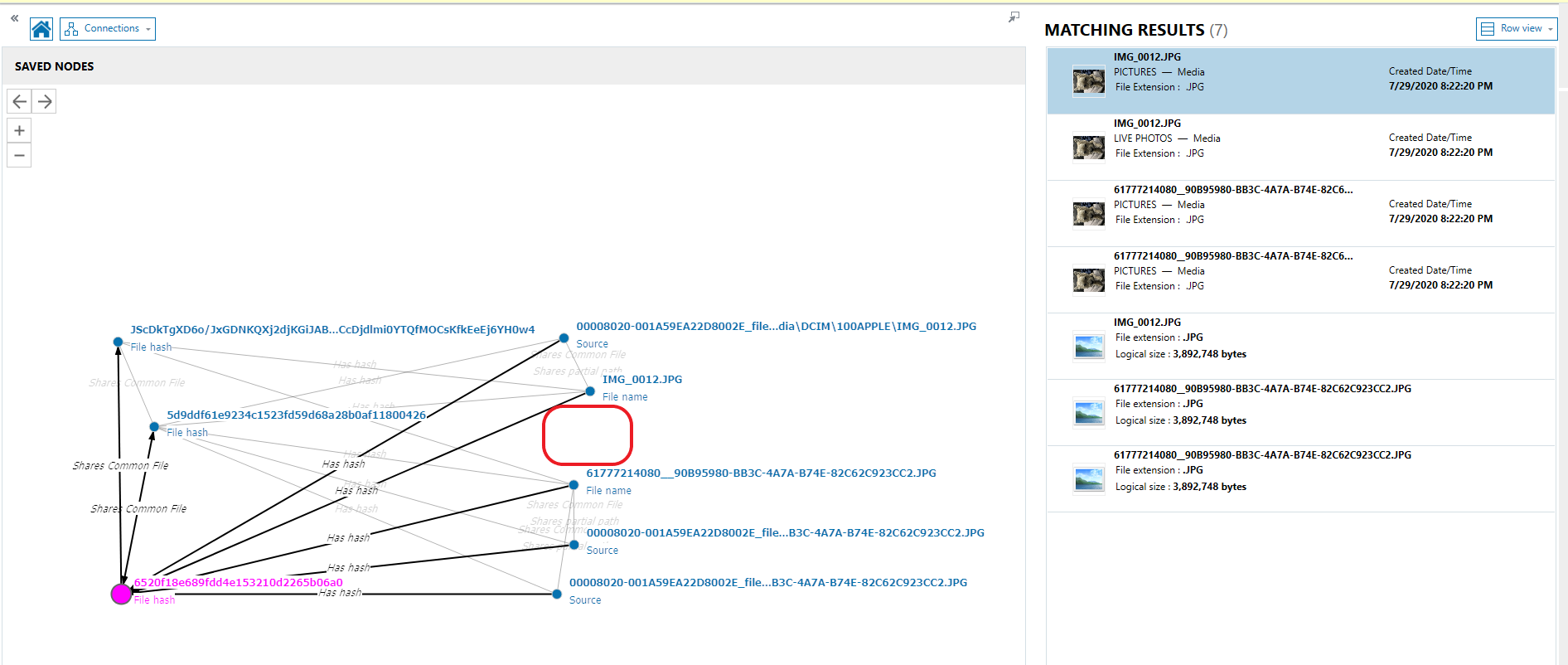
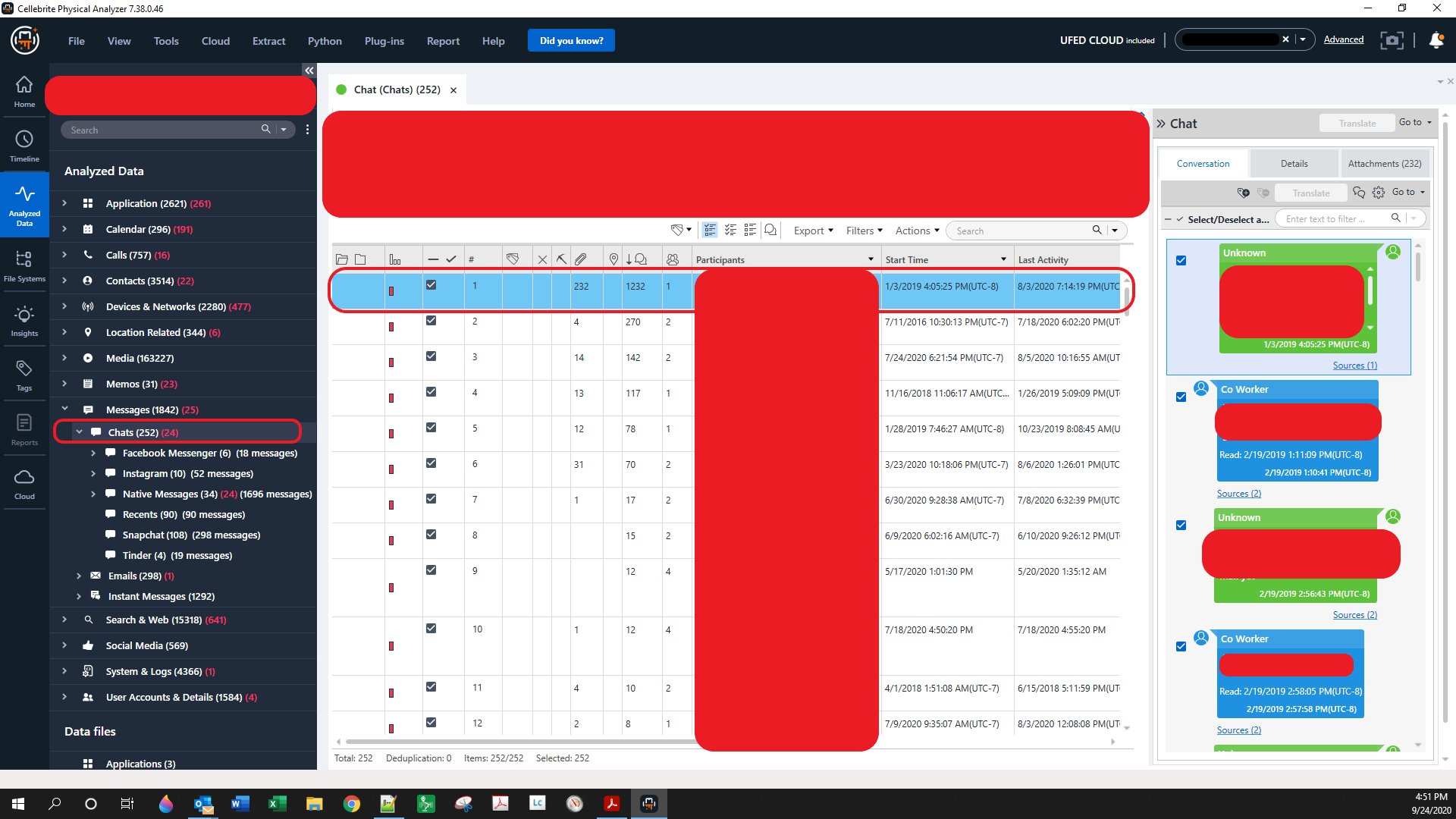
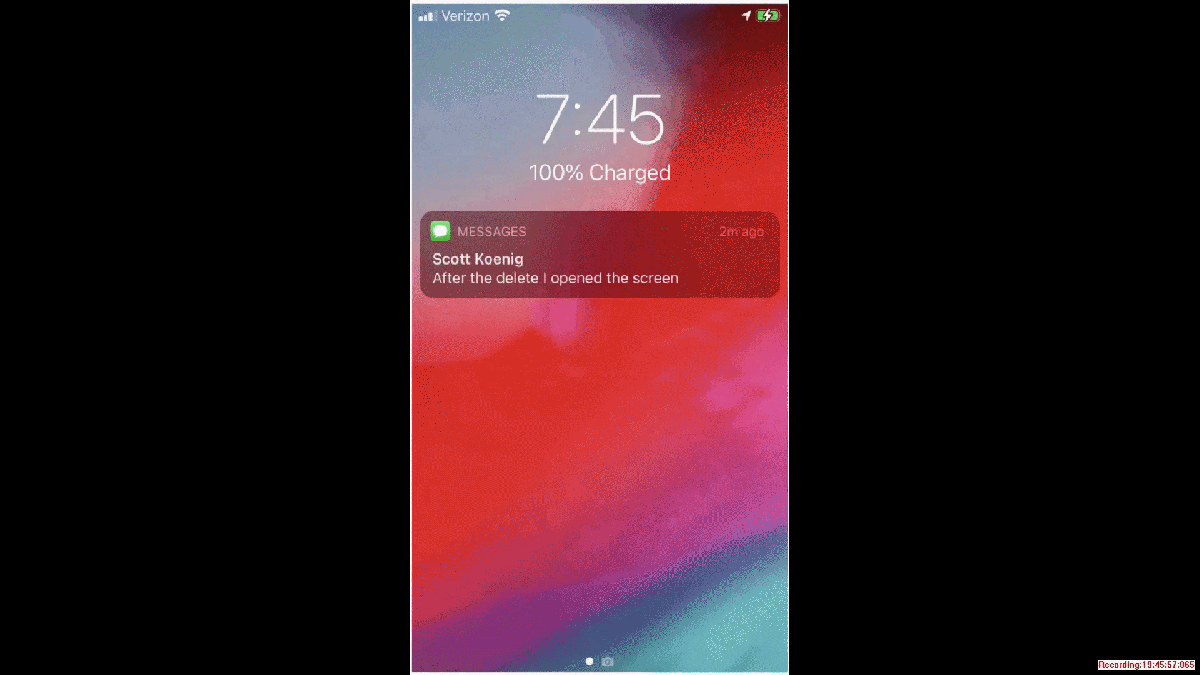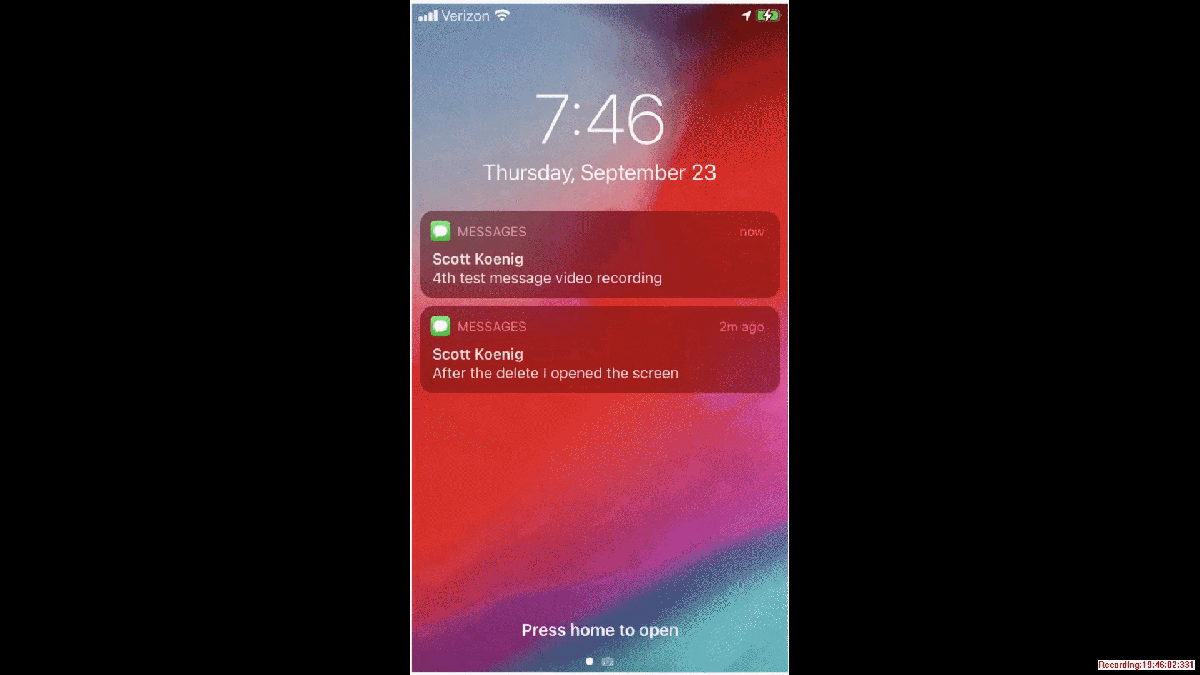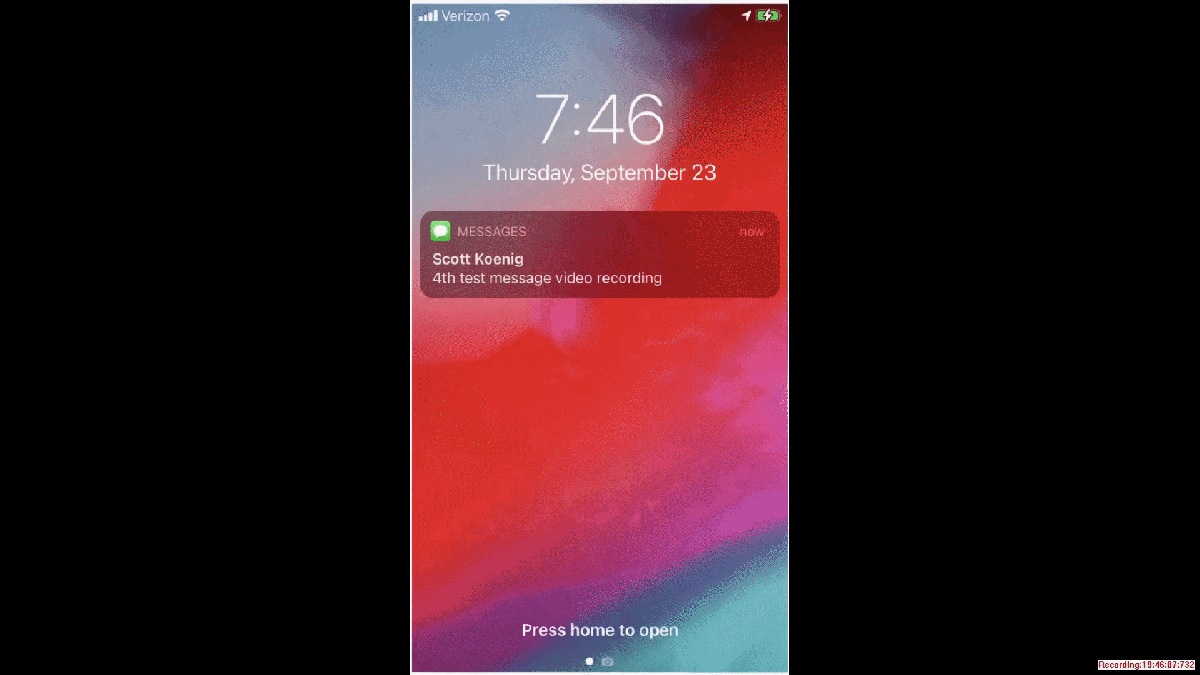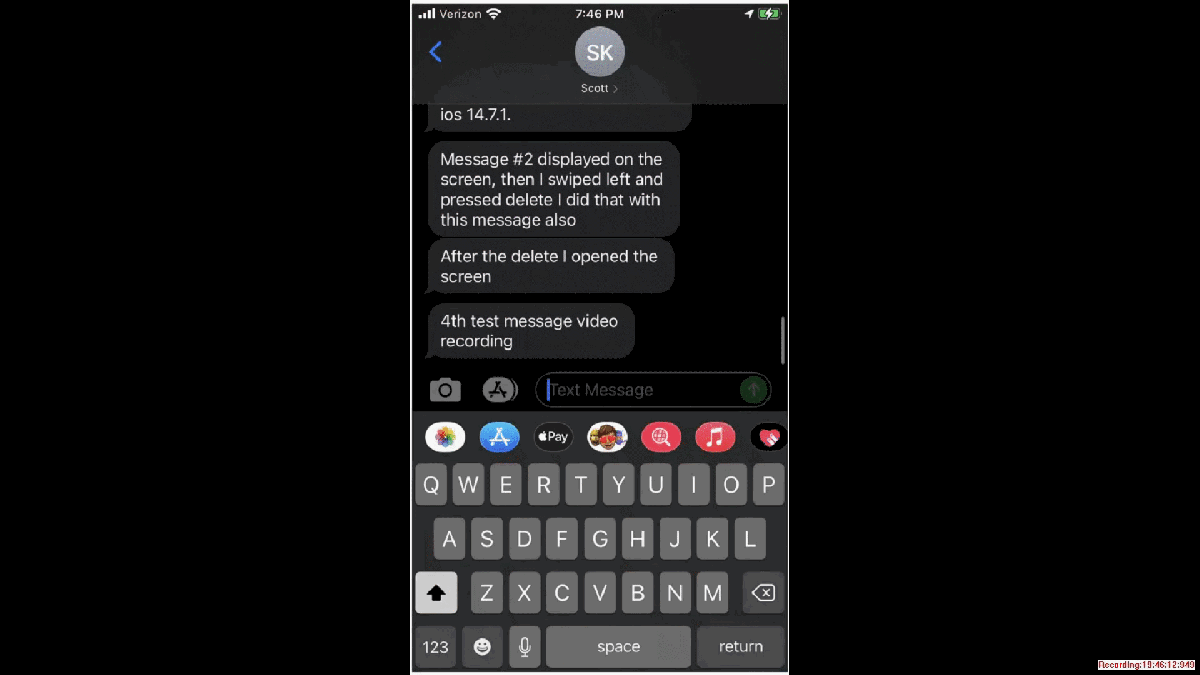
 ️ when using the merge duplicate setting in PA. I would encourage you to view your device data with that setting turned off when you first analyze the data. PA uses the hash of a file, the name of a file and other algorithms to determine if a file is a duplicate. I have found that the same file (hash match) can exist in different file locations and the files existing in the different file locations could indicate a user's interaction. Thus if you merge duplicates you will not see items being placed in the timeline in their appropriate location chronologically. Very similarly to what you are seeing in your screenshot. Here is a short video demonstrating some differences in merge and not merge.
️ when using the merge duplicate setting in PA. I would encourage you to view your device data with that setting turned off when you first analyze the data. PA uses the hash of a file, the name of a file and other algorithms to determine if a file is a duplicate. I have found that the same file (hash match) can exist in different file locations and the files existing in the different file locations could indicate a user's interaction. Thus if you merge duplicates you will not see items being placed in the timeline in their appropriate location chronologically. Very similarly to what you are seeing in your screenshot. Here is a short video demonstrating some differences in merge and not merge. 












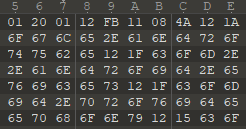














 ️ i will get some sleep and check that out in the morning...thank you 1000x
️ i will get some sleep and check that out in the morning...thank you 1000x










 unsupported (PA)... so have to do manually
unsupported (PA)... so have to do manually 


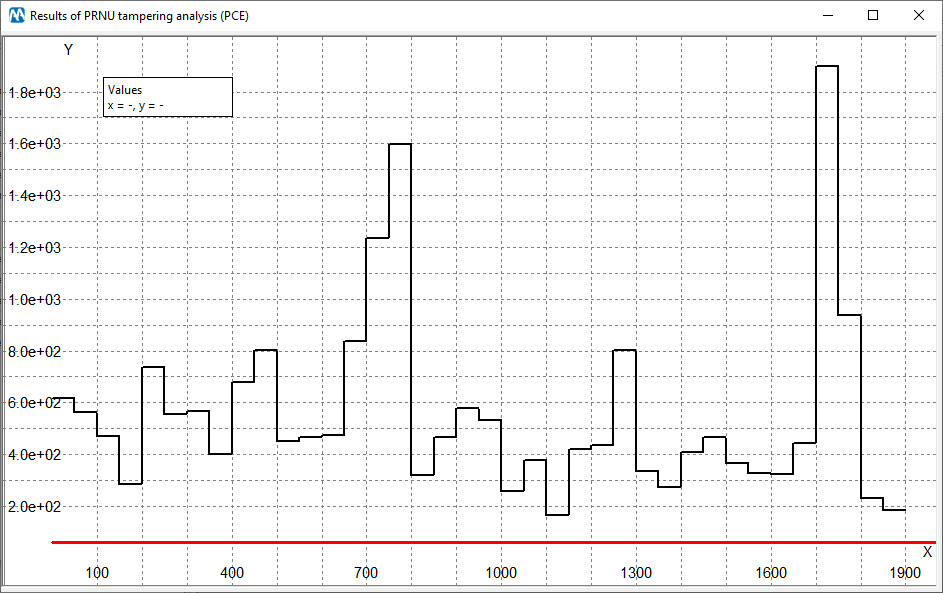








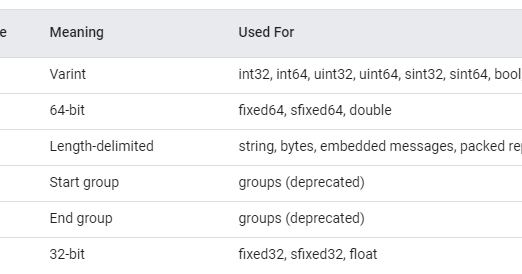




















































 or whatever
or whatever 







 Also Googled the S#$& out of it and can't find them mentioned in any papers or blogs. Currently loading a test device to try and figure it out but was hopeful someone may have already figured it out.
Also looked through apple development docs and couldn't find the list.
Also Googled the S#$& out of it and can't find them mentioned in any papers or blogs. Currently loading a test device to try and figure it out but was hopeful someone may have already figured it out.
Also looked through apple development docs and couldn't find the list.



























































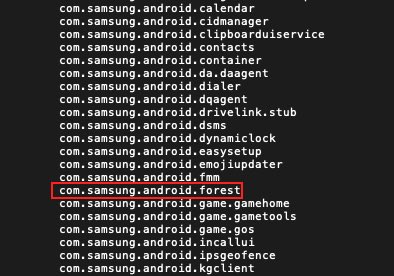





 Andriller - is software utility with a...
Andriller - is software utility with a...









 ️
Healthdb_secure.sqlite —> “samples” table has the column “data_type”. Anyone has a up to date list of known values? I’m looking for info on values 173, 182-188. My google-fu has failed me in getting info on the mentioned values
️
Healthdb_secure.sqlite —> “samples” table has the column “data_type”. Anyone has a up to date list of known values? I’m looking for info on values 173, 182-188. My google-fu has failed me in getting info on the mentioned values 





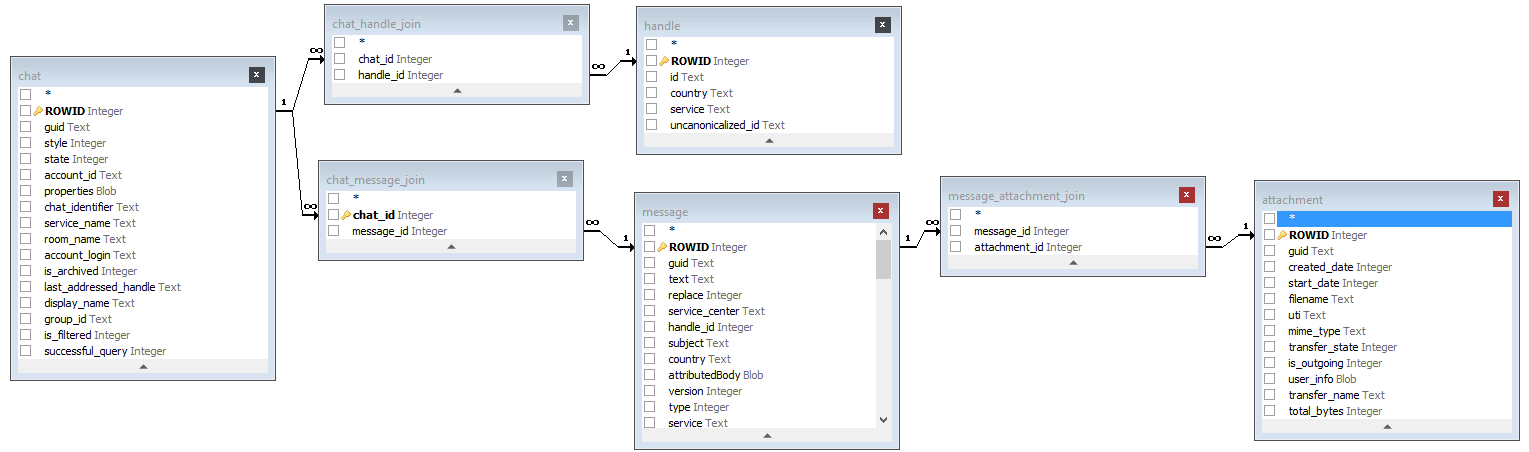
 ️ Drop the keychain in the iLEAPP/scripts/keychain directory first.
️ Drop the keychain in the iLEAPP/scripts/keychain directory first.









































 Memes successfully decrypted
Blogpost:
Memes successfully decrypted
Blogpost:






























 Direct messages
Direct messages







 Decrypts photos, videos, & pin.
Decrypts photos, videos, & pin.
 Thanks to Theincidentalchewtoy for the research & initial code. Read the blogpost:
Thanks to Theincidentalchewtoy for the research & initial code. Read the blogpost:  Get ALEAPP here:
Get ALEAPP here: 











 Access app encrypted media
Access app encrypted media












































































 ️ or
️ or 





 ⬆️ for the link to the blog to the write-up.
⬆️ for the link to the blog to the write-up.
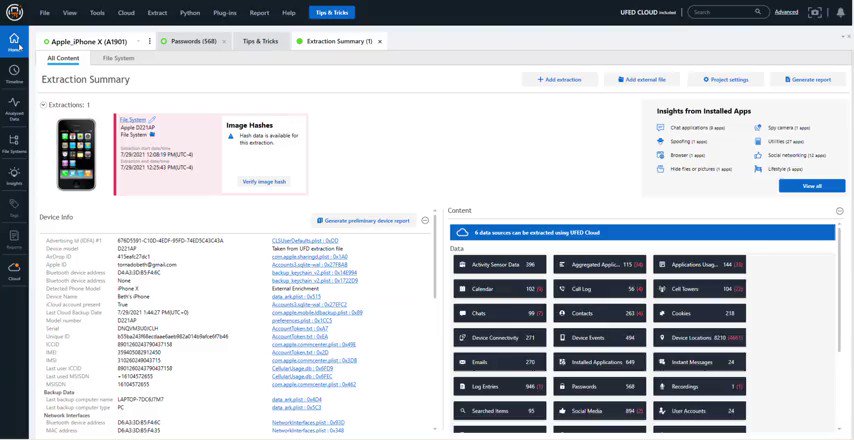













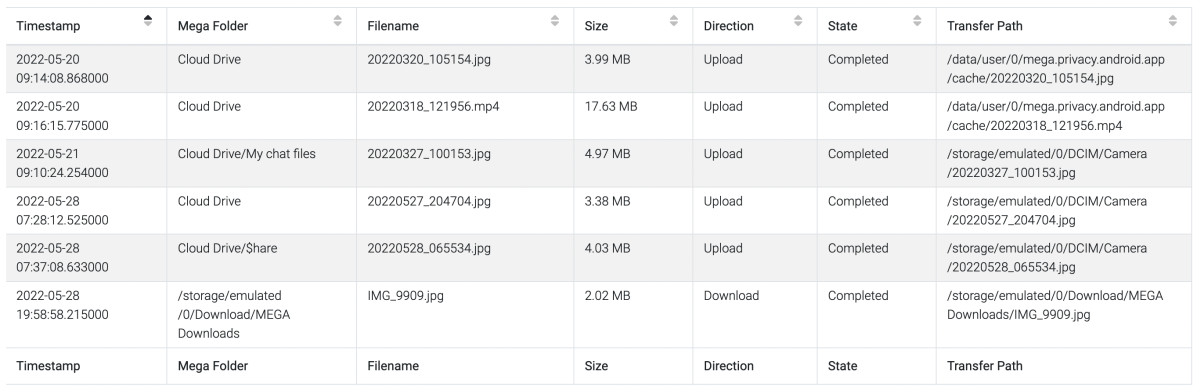
 we need a solution... sooon...
we need a solution... sooon... 


 Photos.sqlite queries have been updated. Research & write-ups will follow. Here are the queries when you need them.
Photos.sqlite queries have been updated. Research & write-ups will follow. Here are the queries when you need them.















































 working some
working some  to automatically save message attachments to the Local Photo Library! #iOS15 #iOS16 #FFS #DFIR
to automatically save message attachments to the Local Photo Library! #iOS15 #iOS16 #FFS #DFIR


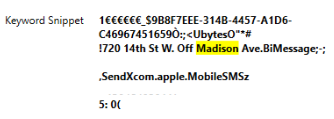










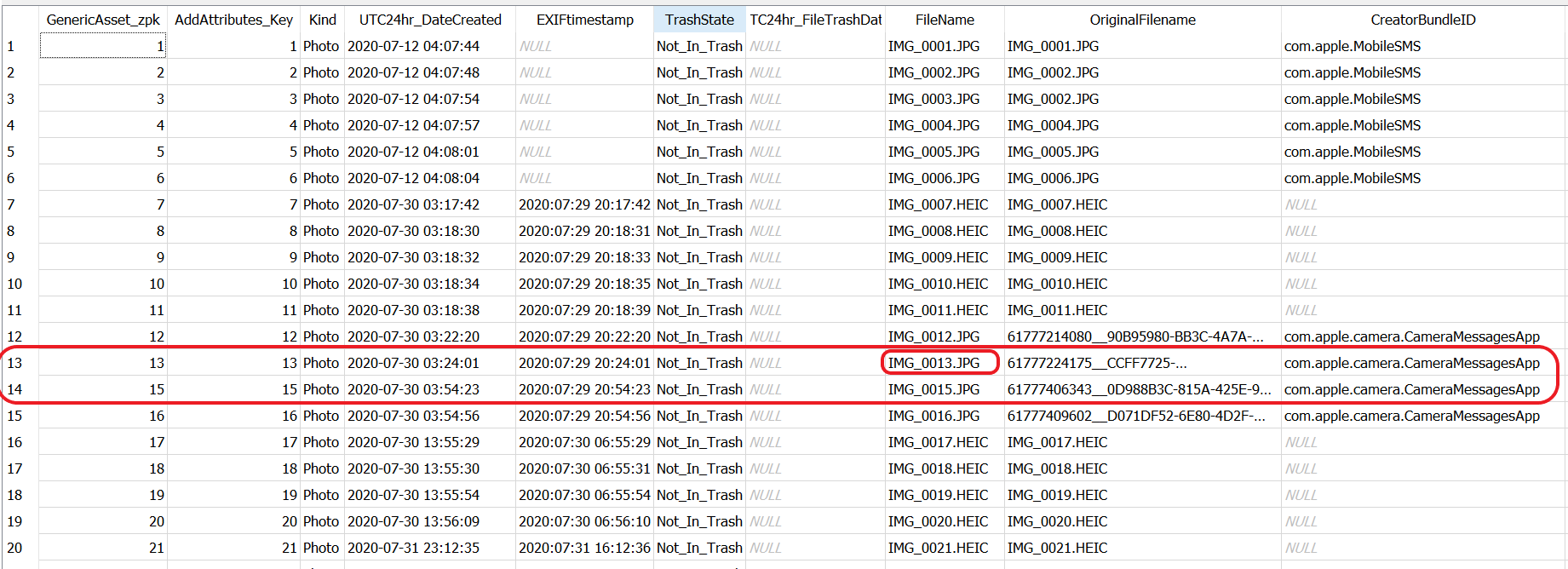
 Thanks to lots of recent feedback a NEW smaller query has been posted for each iOS version (11-16) Local PL Photos.sqlite. This query is focused on the asset:
Thanks to lots of recent feedback a NEW smaller query has been posted for each iOS version (11-16) Local PL Photos.sqlite. This query is focused on the asset:
 UUIDs
UUIDs
 ️File Names
⌚️Timestamps
️File Names
⌚️Timestamps
 Album Titles
Album Titles
 ️Trash status
️Trash status









 ️ winded answer but:
If the assets zAddAssetAttr.ZIMPORTEDBY is Third-Party-App-3 or Third-Party-App-6 than that particular asset was imported into the Local Photo Library via the application listed in the following columns:
zAddAssetAttr.ZIMPORTEDBYBUNDLEIDENTIFIER
zAddAssetAttr.ZIMPORTEDBYDISPLAYNAME
That doesn’t necessarily mean it was captured with that application, it just means that it was imported by that application into the Local Photo Library.
To determine if that application was used to capture the asset, further analysis would be needed.
This is difficult to answer because the analysis needed is reliant upon logs that are only stored for an average of 7-30 days. So if you have an asset that is older than that you might not be able to answer that question confidently.
You will want to look at KnowledgeC, CurrentPowerLog.PLSQL, now with iOS 16 biomes data, and even sysdiagnose to determine if the device camera was being used at the time of capture and creation listed in Photos.sqlite.
You can also analyze exif date, creation date, and add date. If those are similar than you might have an asset that was likely captured with the analyzed device, but you would still need the logs to determine if that device camera was on at the time of the capture.
It is possible, but the ideal situation would be if the device was acquired within 7 days of the captured asset.
Another area of analysis that I haven’t discussed would be the analysis of the third party apps settings. The question I would hope to answer during the analysis of the 3rd party app setting would be: Does the app settings indicate automatic save to the Local Device upon captured media?
Of course, this would be different for every app and I don’t have the answer for where that data would be stored for each app.
️ winded answer but:
If the assets zAddAssetAttr.ZIMPORTEDBY is Third-Party-App-3 or Third-Party-App-6 than that particular asset was imported into the Local Photo Library via the application listed in the following columns:
zAddAssetAttr.ZIMPORTEDBYBUNDLEIDENTIFIER
zAddAssetAttr.ZIMPORTEDBYDISPLAYNAME
That doesn’t necessarily mean it was captured with that application, it just means that it was imported by that application into the Local Photo Library.
To determine if that application was used to capture the asset, further analysis would be needed.
This is difficult to answer because the analysis needed is reliant upon logs that are only stored for an average of 7-30 days. So if you have an asset that is older than that you might not be able to answer that question confidently.
You will want to look at KnowledgeC, CurrentPowerLog.PLSQL, now with iOS 16 biomes data, and even sysdiagnose to determine if the device camera was being used at the time of capture and creation listed in Photos.sqlite.
You can also analyze exif date, creation date, and add date. If those are similar than you might have an asset that was likely captured with the analyzed device, but you would still need the logs to determine if that device camera was on at the time of the capture.
It is possible, but the ideal situation would be if the device was acquired within 7 days of the captured asset.
Another area of analysis that I haven’t discussed would be the analysis of the third party apps settings. The question I would hope to answer during the analysis of the 3rd party app setting would be: Does the app settings indicate automatic save to the Local Device upon captured media?
Of course, this would be different for every app and I don’t have the answer for where that data would be stored for each app.




 on an asset in
on an asset in 





































































 Dynamic App Finder or the free tool Magnet Custom Artifact Generator (MCAG) may work to build a custom artifact for the decrypted copy of the db you've got.
Dynamic App Finder or the free tool Magnet Custom Artifact Generator (MCAG) may work to build a custom artifact for the decrypted copy of the db you've got.


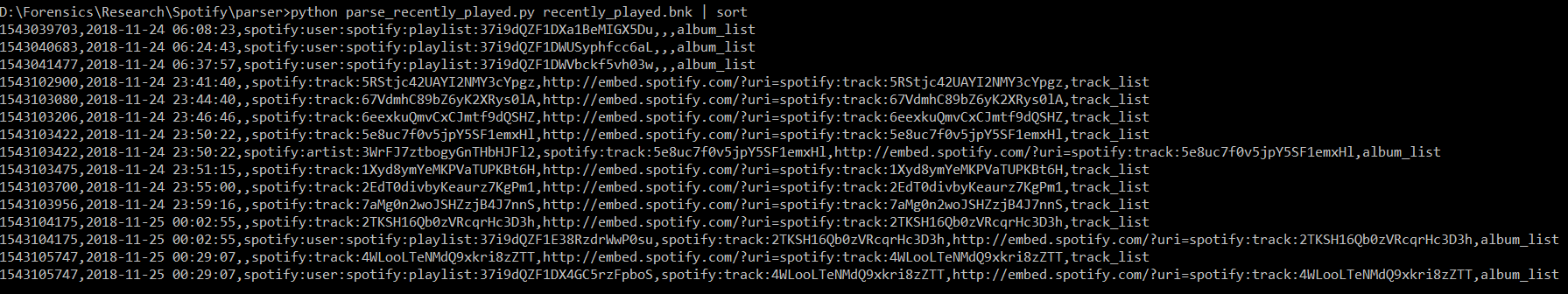














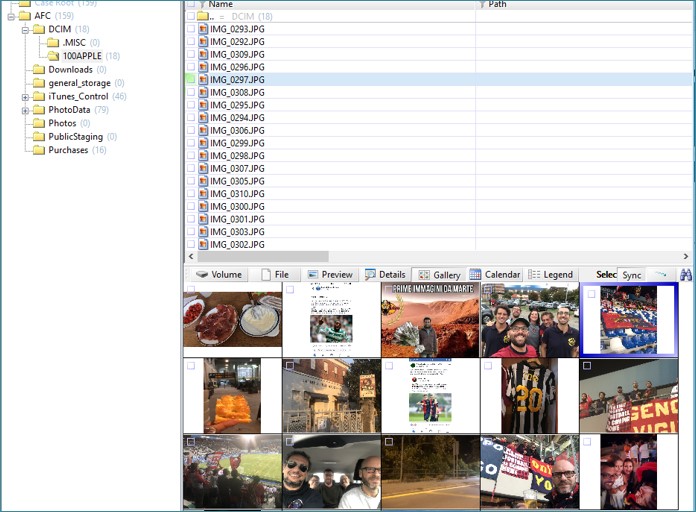










 ©️ (@Loicforensic@infosec.exchange)
©️ (@Loicforensic@infosec.exchange)







































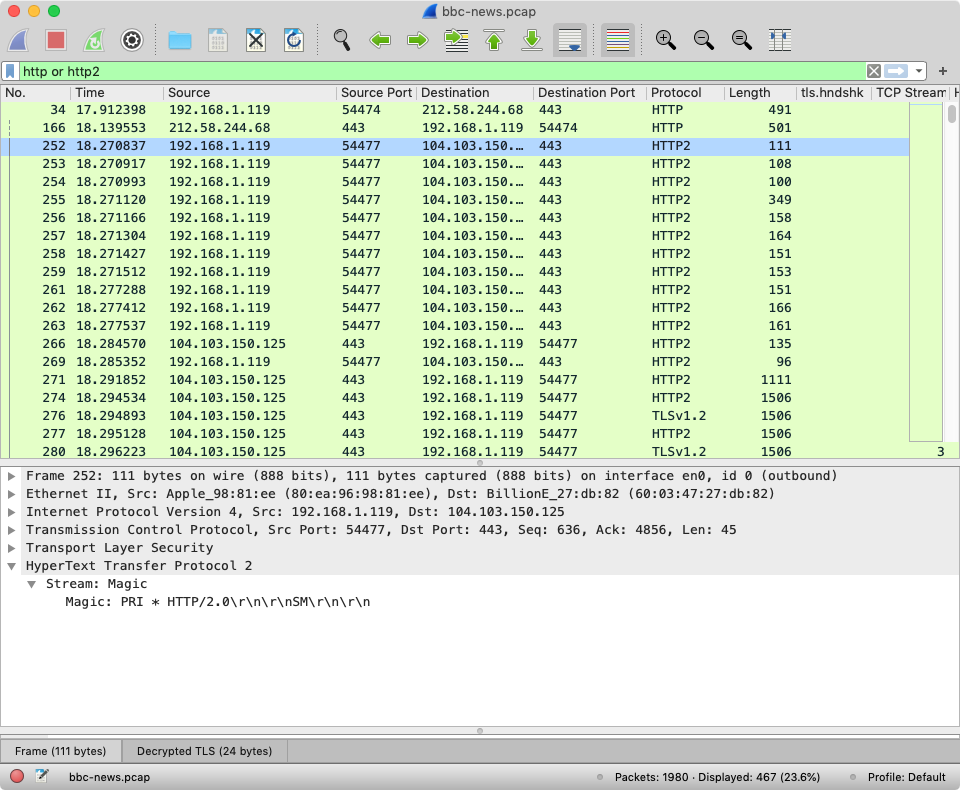


















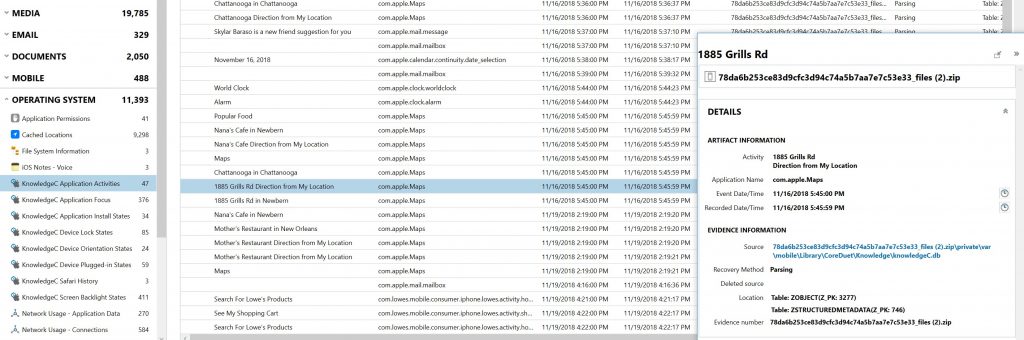








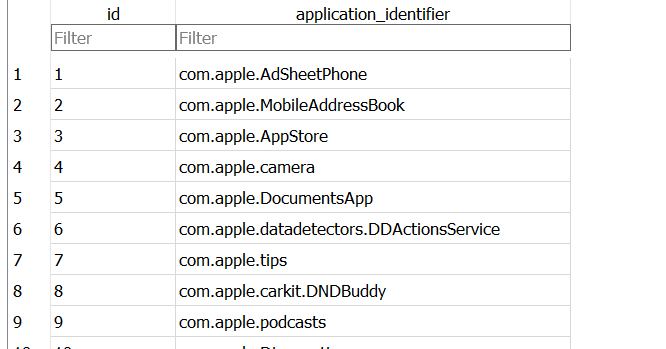



















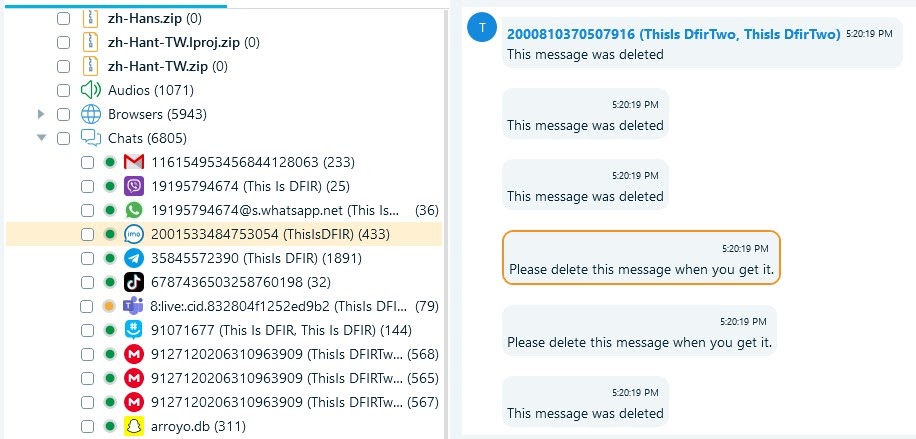
















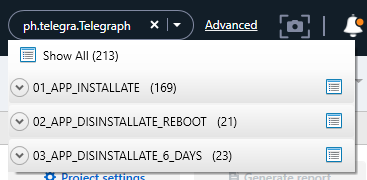







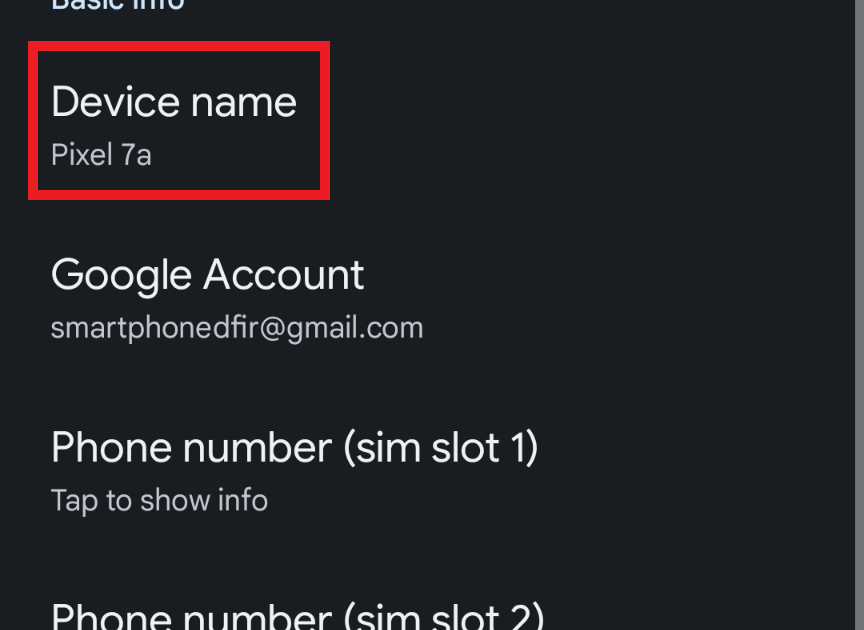


























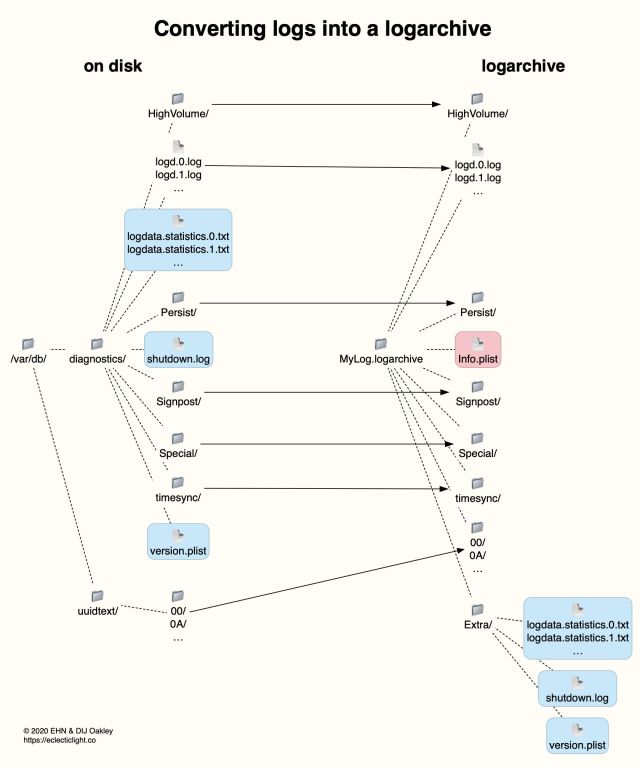




















 ️ts, I go to installed applications and click the source link to find the GUID quickly.
️ts, I go to installed applications and click the source link to find the GUID quickly.













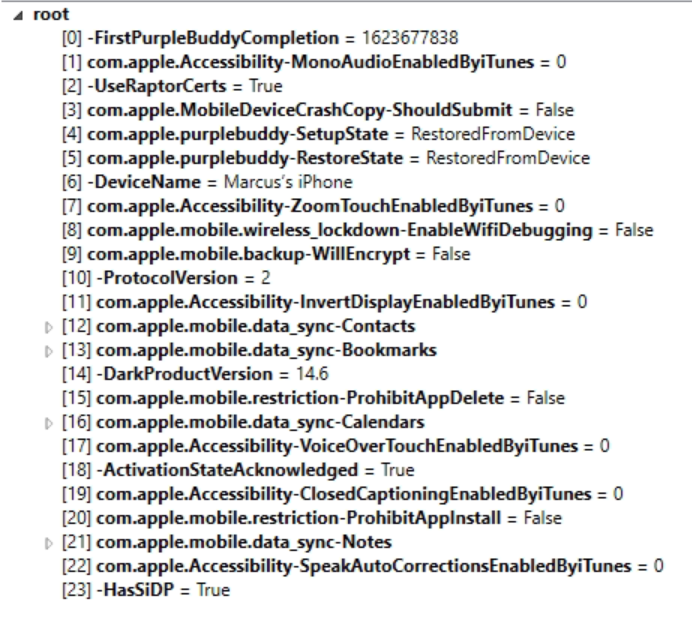




 artifacts or derived from the smoking
artifacts or derived from the smoking  & required in-depth forensic analysis?
& required in-depth forensic analysis?







 Edit: I've looked at the UserID but suspect it's just the ID for the account itself and not connected to the device it self. Can't see any coordinates either.
Edit: I've looked at the UserID but suspect it's just the ID for the account itself and not connected to the device it self. Can't see any coordinates either.








































 ️
️








